 Choosing
security settings
Choosing
security settings Choosing
security settings
Choosing
security settingsYou don't have to make any settings choices to be protected by ZoneAlarm Pro! Read below to learn how the default settings protect you from hacker threats.
![]() Tip
If you are an expert computer user and you want to take control of the details
of your security, see the related topic Customizing your security.
Tip
If you are an expert computer user and you want to take control of the details
of your security, see the related topic Customizing your security.
In choosing Internet security settings, your goal is to ensure the highest possible security with the least loss of Internet convenience.
Our security professionals have chosen ZoneAlarm Pro's default security settings with this double goal in mind. They protect your computer from harm and safeguard your information, while keeping your Internet experience convenient.
Example: Cookie control
Internet cookies make it possible for e-commerce sites (like Amazon, for example) to recognize you as soon as you arrive and customize the pages you visit. However, cookies can also be used to record information about your Web-surfing habits and give that information to marketers and advertisers.
Zone Alarm Pro's default medium cookie control setting balances security with convenience by blocking only third-party cookies—those cookies that are used to track your viewing habits. Session cookies and persistent cookies are allowed.
If you wish, you can instantly block all cookies by choosing the high cookie-control setting, giving you have full protection against all types of cookie abuse—-but at the expense of the convenience that cookies make possible.
For most people, the default settings chosen by the security professionals at Zone Labs provide strong security without sacrificing too much convenience and interactivity.
|
Control |
Default |
What the default setting does |
|
Firewall-Internet Zone |
 |
Makes your computer invisible to hackers. Traffic to or from the Internet Zone is blocked, unless it is initiated by a program on your computer that you've given permission to communicate with the Internet Zone. |
|
Firewall- Trusted Zone |
 |
Enables you to share files and printers with computers on your home or local network. |
|
Program Control-Authentication |
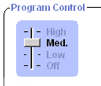 |
Programs must ask for permission and be authenticated before communicating with the Internet.
|
|
Alerts & Logs |
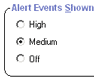 |
Only high rated alerts are be shown. This keeps you from being interrupted unnecessarily. |
|
Privacy - Cookies |
 |
Session cookies and persistent cookies are allowed, but third-party cookies are blocked. This lets you benefit from the convenience of cookies, while preventing advertisers and other third parties from getting information about your Internet habits. |
|
Privacy - Ad blocking |
 |
Blocks pop-up ads and banner and skyscraper ads that take more than a few seconds to load. Ads that don't slow down Internet performance are allowed. |
|
Privacy - Mobile Code |
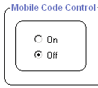 |
While mobile code can be a vulnerability, it also is a powerful tool for making Web sites interactive. Mobile code control is turned OFF by default to let you take advantage of that interactivity. |
|
E-mail Protection |
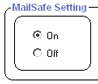 |
Quarantines 46 common types of e-mail attachments, like executable files (.exe) and MS-DOS applications(.com), that can contain worms or viruses. |
| Web Filtering-Parental Control |  |
Blocks undesirable Web sites, such as those containing violence or pornography. |
| Web Filtering-Smart Filtering |  |
Enables the filtering of new Web sites that have not yet received ratings. |
Customizing your security
Program authentication
cookie
A small data file used by a Web site to customize content, remember you from
one visit to the next, and/or track your Internet activity. While there are
many benign uses of cookies, some cookies can be used to divulge information
about you without your consent.
session cookie
A cookie stored in your browser\'s memory cache that disappears as soon as you
close your browser window. These are the safest cookies because of their short
life-span.
persistent cookie
A cookie put on your hard drive by a Web site you visit. These cookies can be
retrieved by the Web site the next time you visit. While useful, they create
a vulnerability by storing information about you, your computer, or your Internet
use in a text file.
third party cookie
A persistent cookie that is placed on your computer, not by the Web site you
are visiting, but by an advertiser or other \'third party.\' These cookies are
commonly used to deliver information about your Internet activity to that third
party.
component
A small program or set of functions that larger programs call on to perform
specific tasks. Some components may be used by several different programs simultaneously.
Windows operating systems provide many component DLLs (Dynamic Link Libraries)
for use by a variety of Windows applications.
quarantine
ZoneAlarm Pro's MailSafe quarantines incoming e-mail attachments whose filename
extensions (for example, .EXE or .BAT) indicate the possibility of auto-executing
code. By changing the filename extension, quarantining prevents the attachment
from opening without inspection. This helps protect you from worms, viruses,
and other malware that hackers distribute as e-mail attachments.